Introduction
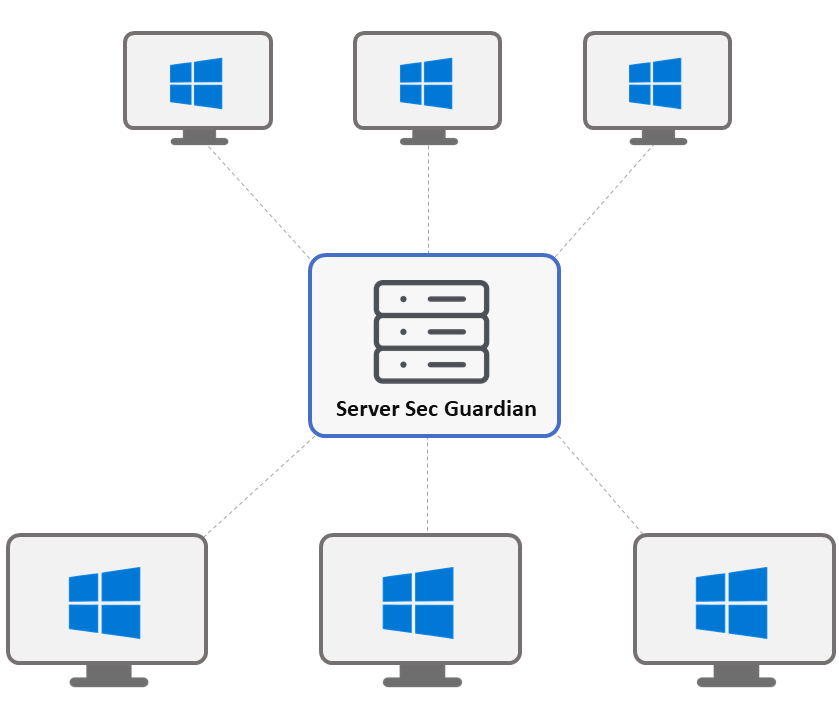
Different view of endpoint protection
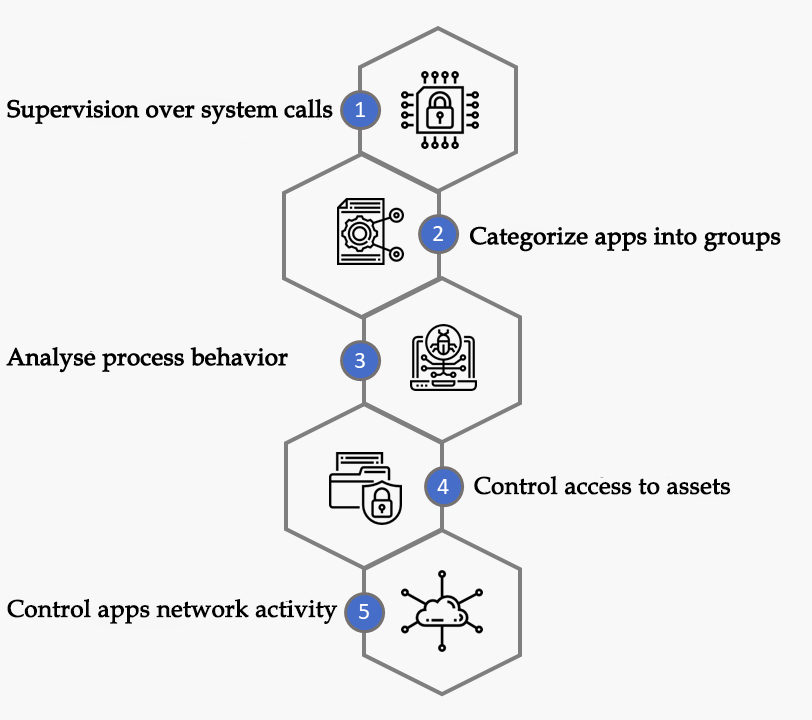
Classic antivirus solutions are no longer sufficient for reliable data protection of nowadays targeting hacker attacks on company data, zero-day attacks, or persistent threats like ransomware.
Standard security methods protecting end point workstations must be supplemented by an additional security layer based on computer behavior analysis capable of detecting so far unknown threats.
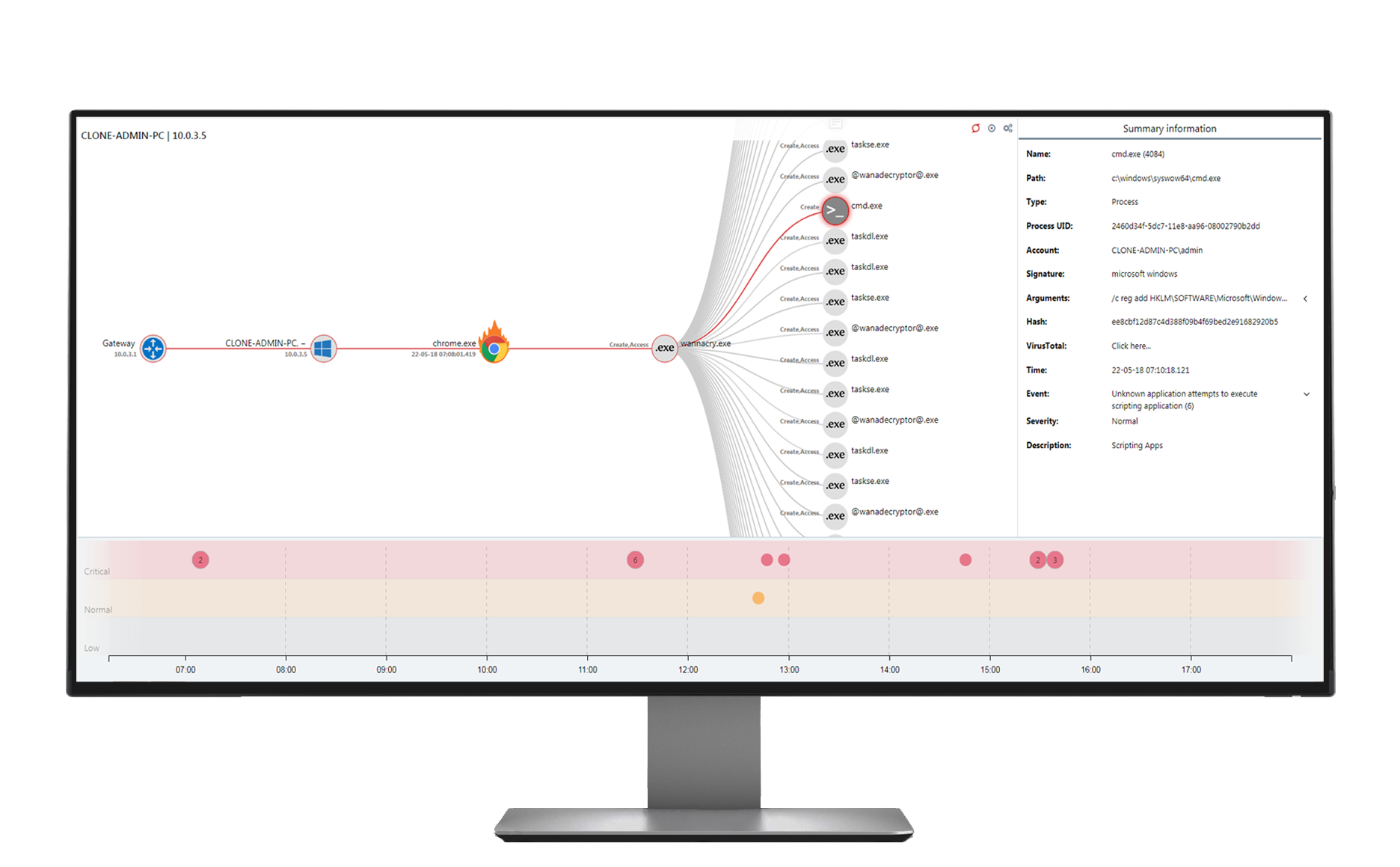
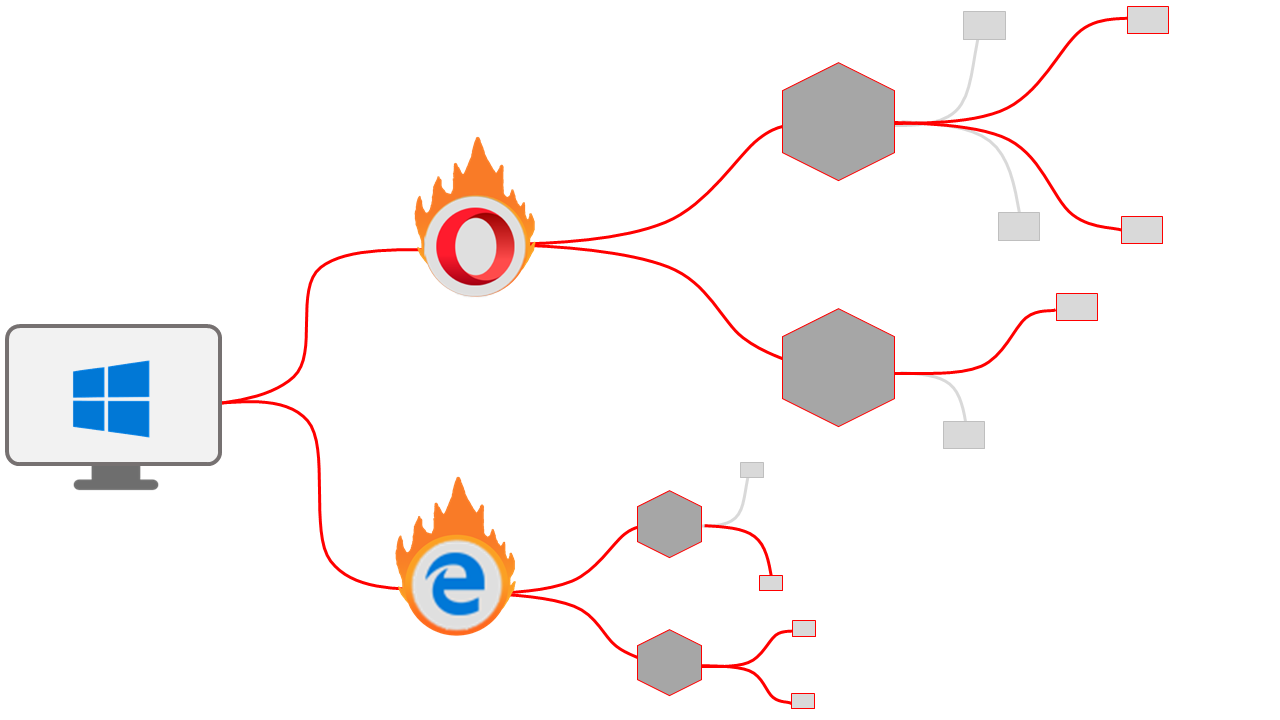
Exploit Guardian protects applications with vulnerable security holes of critical and very vulnerable applications such as web browsers, system files, PDF editors, etc. It monitors the behavior of processes in memory and evaluates, reports, and blocks threats based on the deciding algorithm associated with system activities.